
Förderjahr 2020 / Stipendien Call #15 / ProjektID: 5294 / Projekt: Trustworthy Context-Aware Access Control in IoT Environments based on the Fog Computing Paradigm
Trust in computer networks
Conceptually, trust represents "measurable belief and/or confidence which represents accumulated value from history and the expecting value for the future" [1]. Being influenced by multiple factors: the reputation of entities, relationships between them, human decision, quantification of trust is a complex process. For that reason, establishing trustworthy IT system does not involve merely devices and network, but also human trust in the IT system.
In the area of computer networks, trust is scoped through the Trustworthy Networking (TN), which incorporates a set of methods with the goal of provisioning reliable and secure communications between network entities (trustor and trustee) that have established trust relationships [2]. These entities are grouped within a TND, characterized by administrative features with a certain trust level and established mutual trust relationships between all of its members.
Achieving trustworthy networks
As described in the previous blog, secure communication is defined through the CIA model, which is most often ensured by encrypting the communication link and the transferred data. Additionally, mutual trust relationships between network peers required unfalsifiable identity proof, provided through peer authentication. Thus, trust management heavily relies on the secure management of secrets (keys) and identities through the network, which network peers will use to prove their trustworthiness.
Key Management (KM) has its ultimate goal in providing a consistent state concerning disseminated keys. Thus, KM has to provide several features: creation, validation, revocation, and expiration. The attached graphic presents the primary aspects with regard to key management. In the scope of this blog, we will dive into KM aspects concerning trust modeling.
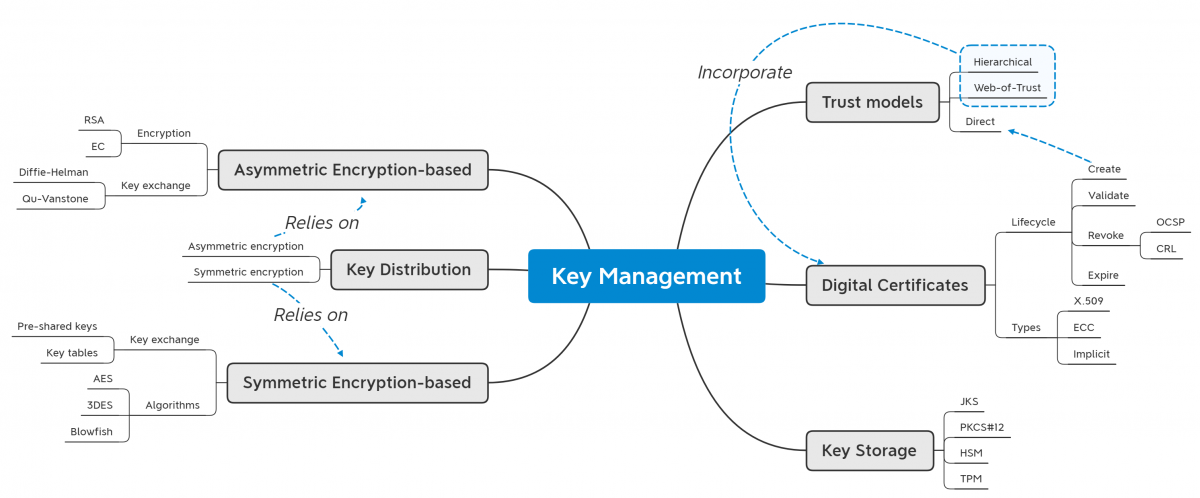
Modeling trust between network peers
Trust models employ various organization strategies concerning the management of security material, depending on the scenario for which they are used. These strategies are split into three main models: (1) Direct trust, (2) Web of Trust, and (3) Hierarchical trust [3].
In a Direct trust model, trustor and trustee exchange their secrets and establish trust relationships in a manner that is immediately convincing to them, that is, without the need for the trusted third-party. Application of direct trust model in network mostly involves the distribution of symmetric key pair during manufacturing or system integration, thus enabling data confidentiality and integrity, as well as entity authenticity during the system's runtime. However, this approach puts up a burden for the trust maintenance through key management during the system's runtime since any secret revocation and renewal has to be propagated to every entity in the network.
The Web of Trust (WoT) model utilizes trust propagation between peers for improving trust management in dynamic environments. Namely, in a WoT, the trustor can establish trust relationships with a trustee if the credentials of the trustee are trusted by another entity that has already established trust relationships with the trustor. This model is employed in Pretty Good Privacy (PGP), where individual nodes maintain a list of trusted public keys. While WoT improves support for networks' dynamic (peers entering/leaving the TND) compared to the direct trust model, it still does not offer efficient capabilities for non-static networks - e.g., vehicular network, ad-hoc sensor network.
The Hierarchical trust model involves the presence of one or more intermediary entities - Trust Anchor (TA) in the TND, which serve to establish trust relationships between the communicating nodes that do not have previous trust relationships. To gain the ability to act as a trusted intermediary, TAs have to establish trust relationships with all the nodes in the TND, for which they afterward will provision trust relationships. This is established through the exchange of encryption keys before or during the system's runtime, whereas the methods mentioned above are employed. Hierarchical trust is widely employed in computer networks through several standards: Kerberos in corporational networks, X.509 in WWW.
Applying trust models in IoT
So, which model would suit the IoT needs? Direct trust and WoT would hardly scale with the size and dynamicity of IoT networks. In contrast, hierarchical trust heavily relies on asymmetric encryption, which all sensors in IoT networks cannot support. Thus, novel hybrid models are researched world-wide. These models mostly reduce the computational requirements of hierarchical trust so that more sensors can use it. Still, even the lightweight asymmetric encryption consumes significant energy and computational power. Therefore, the mainstream approach is to design protocols that switch from hierarchical trust to direct trust as soon as possible to perform as many KM operations using symmetric encryption.
[1] Y.3052 : Overview of trust provisioning for information and communication technology infrastructures and services. Mar. 2017 (accessed Mar. 8, 2021). url: https://www.itu.int/rec/T-REC-Y.3052-201703-I.
[2] Y.3053 : Framework of trustworthy networking with trust-centric network domains. Jan. 2018 (accessed Mar. 8, 2021). url: https://www.itu.int/rec/T-REC-Y.3053-201801-I.
[3] F. Hu. Security and Privacy in Internet of Things (IoTs): Models, Algorithms, and Implementations. CRC Press, Apr. 2016, pp. 1–564.


