
Förderjahr 2020 / Stipendien Call #15 / ProjektID: 5294 / Projekt: Trustworthy Context-Aware Access Control in IoT Environments based on the Fog Computing Paradigm
IoT has brought the interconnection of many different IoT devices - Things. Still, the sensing capabilities of Things enable a limitless number of novel services that could be implemented to improve IoT environments' usability and applicability and allow further smartification of IoT systems through the self-configuration routines, building the context-aware IoT systems.
Context-Awareness (C-A) and its application have been researched since the 1990s and nowadays attract the IoT system developers' attention since it allows an IoT system to adapt its behavior based on the current system state [1]. Besides improving IoT systems by adding the "intelligent" features, C-A also allows IoT security mechanisms automation. A proper candidate for IoT security automation is the security policy configuration, which can minimize the human effort required to configure the IoT environment's security properties.
Context management - Background
The terms C-A and Context-Aware System (C-AS) have been defined by Dey et al. [2] as "a system is context-aware if it uses context to provide relevant information and/or services to the user, where relevancy depends on the user's task." A context-aware computer system is any computer system able to use the context, i.e., analyze and interpret insights on their environment's current state and adapt provided services and functionalities without the explicit user intervention. The services that a C-AS can offer are grouped as follows:
- Presentation of information to the stakeholders,
- Tagging context to information,
- Active or passive service execution,
- Active or passive service configuration.
So what is the context? And how can we identify, collect, manage, and use the context information?
The answer to the first question is provided in the definition of the context by Dey et al. [2], which states that the context is "any information that can be used to characterize the situation of an entity. An entity is a person, place, or an object relevant to the interaction between a user and an application, including the user and applications themselves". From this definition, context can be anything measurable in the IoT environment, meaning that once the context information we would like to utilize in IoT is chosen, we need to start from the use-case we are building.
Answering the second question is tightly coupled with the concept called C-A lifecycle (see picture below). In the C-A lifecycle, context information is collected, aggregated into the design context model, reasoned using various analysis techniques, and distributed to the context information consumers. Methods, approaches, models, and protocols present in C-A lifecycles' are out of scope for this blog, but the excellent analysis of them is provided by Perera et al. [3].
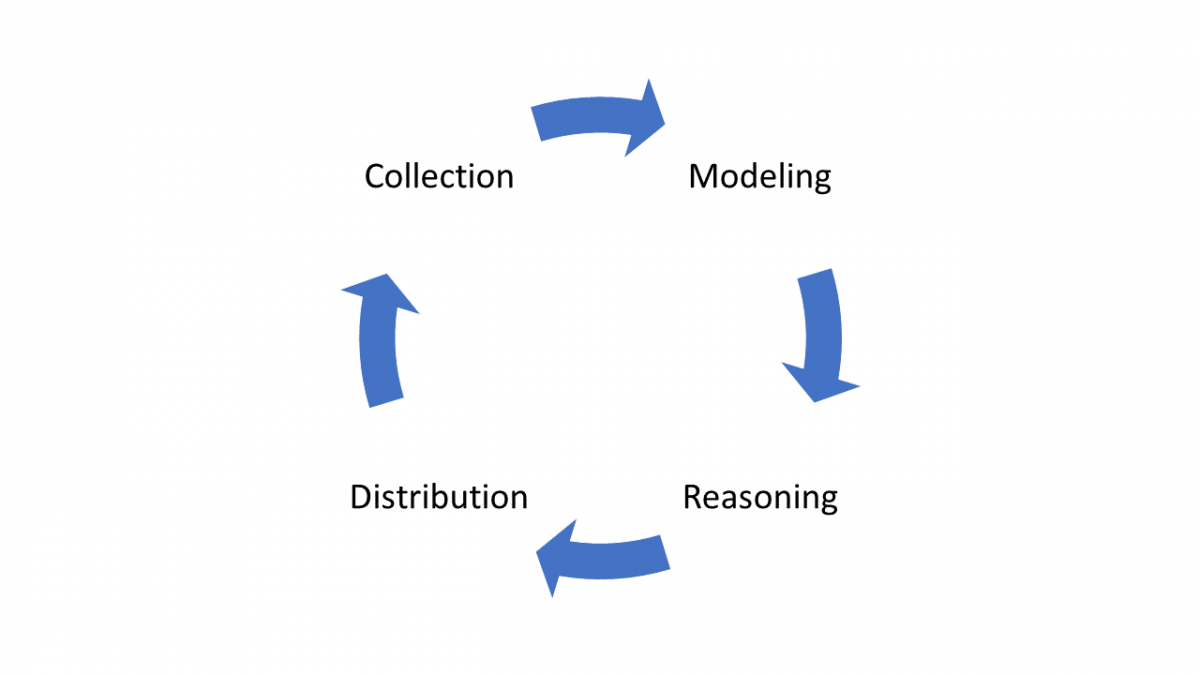
Building Context-Aware Access Control Systems
Having cleared the C-A basics, let's look at how the Access Control (AC) can become C-A-compatible. Every AC system offers the following two features:
- Security policy management
- Authorization - enforcement of the security policies
For that reason, we need to find a way of embedding the context information in these features.
An essential aspect of the first feature is to allow the utilization of the context information as a part of the security attributes - the basic building block of the security policies. For that purpose, we need to pick out a compliant access control model. The previous blog [4] presents multiple access control models. From these models, ABAC and CAPBAC stand out as the best candidates. However, ABAC has an advantage over CAPBAC since CAPBAC relies on precalculated security policies, which can be quite computationally expensive since context information can be very dynamic and cause a lot of unneeded calculations.
For the second AC feature, the AC gateway is required to consume and process the context information. Compared to the traditional authorization, which relies only on the user information contained in the session token, C-A enabled AC gateway has to fetch context information from various context sources, as depicted in the graph below. Fetching context information occurs either through pull or push approaches. The push approach relies on the security attribute values that are notified from the context sources, meaning that the AC gateway has to rely on the other services to obtain the up-to-date context information. Since this process is not 100% reliable and the values of the C-A security attributes can be critical for authorization, AC gateway can pull the data from the context source, therefore obtaining the latest and greatest C-A attribute value.
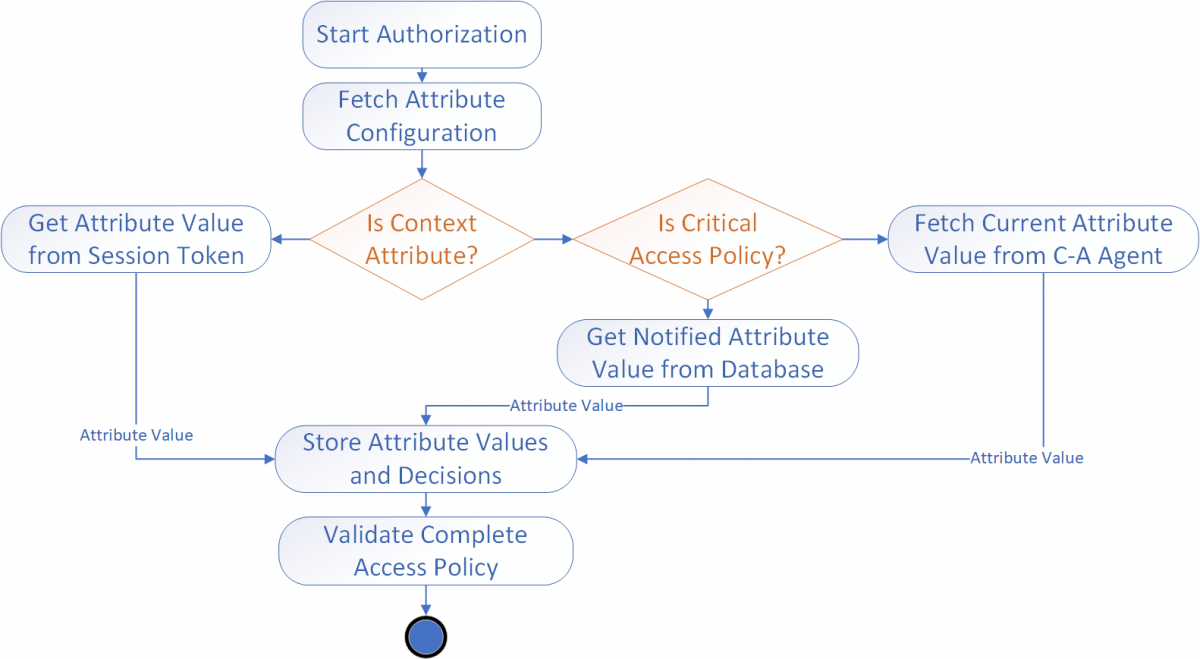
This blog provided the C-A basics and the initial steps for building C-A AC systems. Even though context management in IoT allows numerous novel services, its implementation comes with a cost of computational and network traffic overhead. That is why it is essential to thoroughly analyze the use-cases and approaches for building C-AS since it can introduce energy costs and reduce the IoT services' responsiveness. Still, when appropriately built, C-ASs in IoT dramatically increase the appeal and usability of IoT services, creating intelligent IoT environments!
[1] E. Borgia. “The Internet of Things vision: Key features, applicationsand open issues”. In: Computer Communications 54 (Dec. 2014), pp. 1–31.
[2] Abowd et al. “Towards a Better Understanding of Context and Context-Awareness”. In: HUC 1999: Handheld and Ubiquitous Computing. Nov. 1999.
[3] C. Perera, A. Zaslavsky, P. Christen, and D. Georgakopoulos.“Context Aware Computing for The Internet of Things: A Survey”. In: IEEE Communications Surveys Tutorials 16.1, May 2014
[4] https://www.netidee.at/trustworthy-context-aware-access-control-iot-env…


