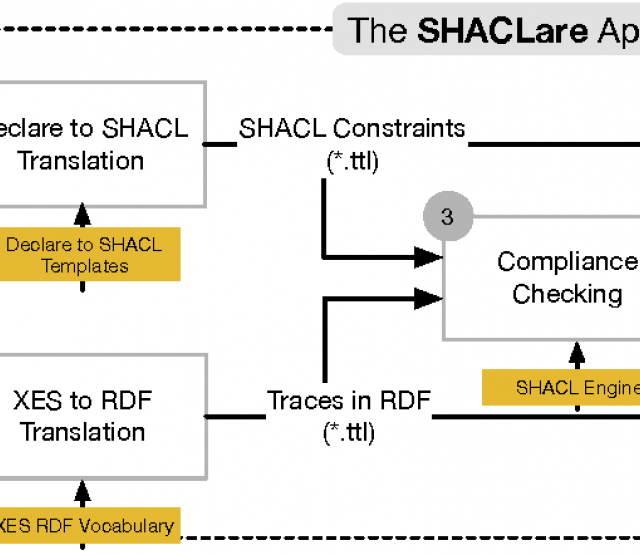
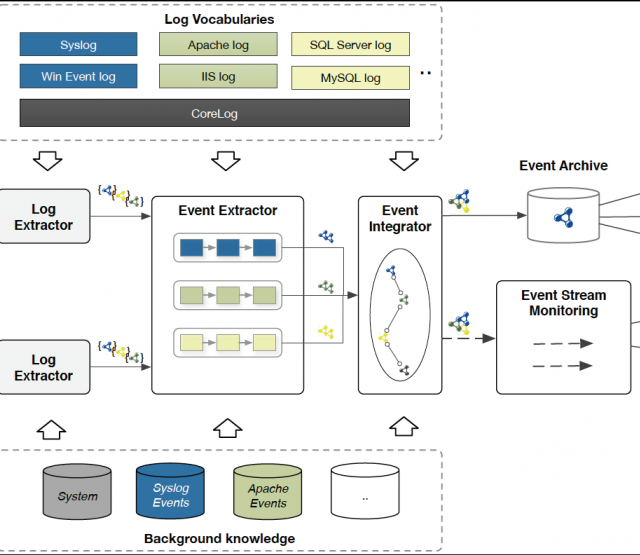
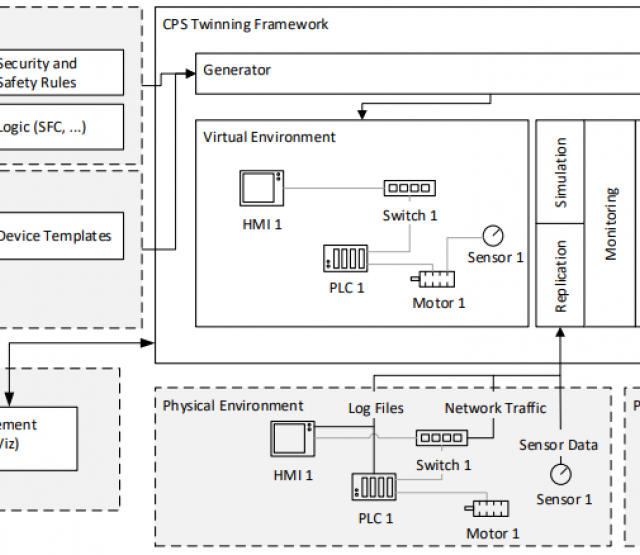
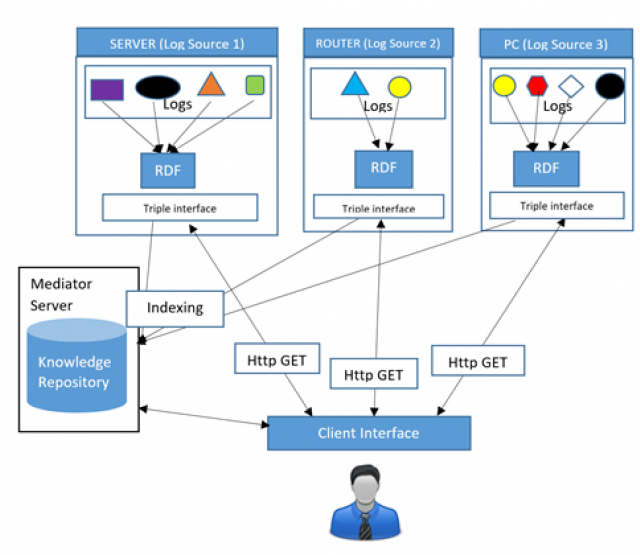
Förderjahr 2017 / Science Call #1 / ProjektID: / Projekt: SEPSES
We are happy to announce that our poster paper title “An ATT&CK-KG for Linking Cybersecurity Attacks to Adversary Tactics and Techniques” has been accepted at the ISWC conference 2021.
The paper discusses an extension of our prior work namely Cybersecurity Knowledge Graph (CSKG) with adversary tactics and techniques to support analysts in connecting log events to higher-level attack steps.
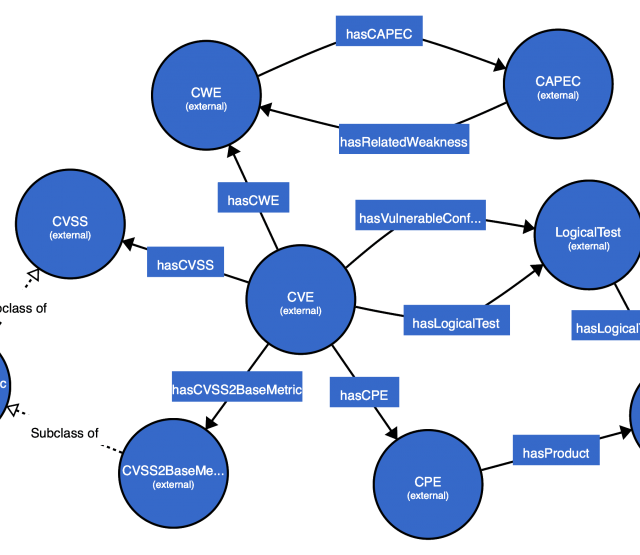
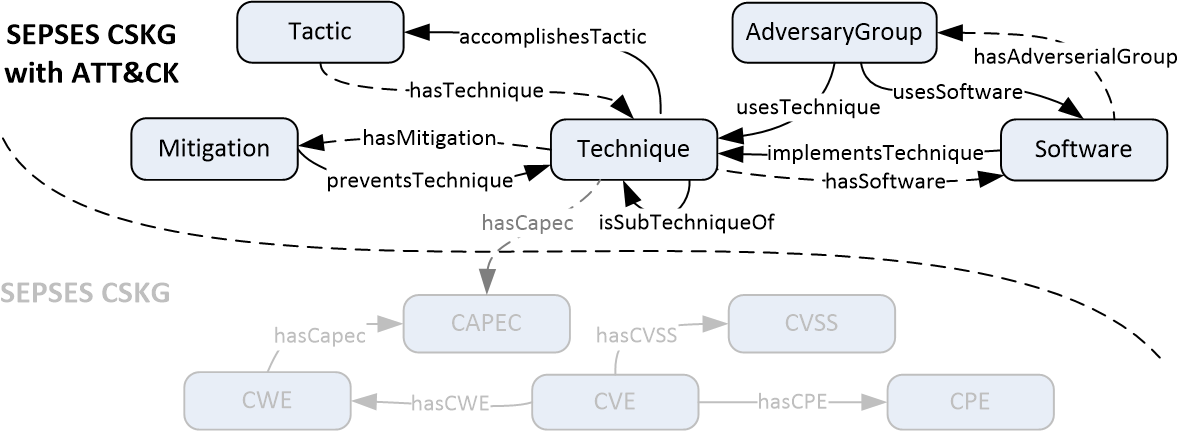
For this purpose, we developed a vocabulary to represent rich threat intelligence instance data from MITRE ATT&CK in a knowledge graph as visualized in the following excerpt:
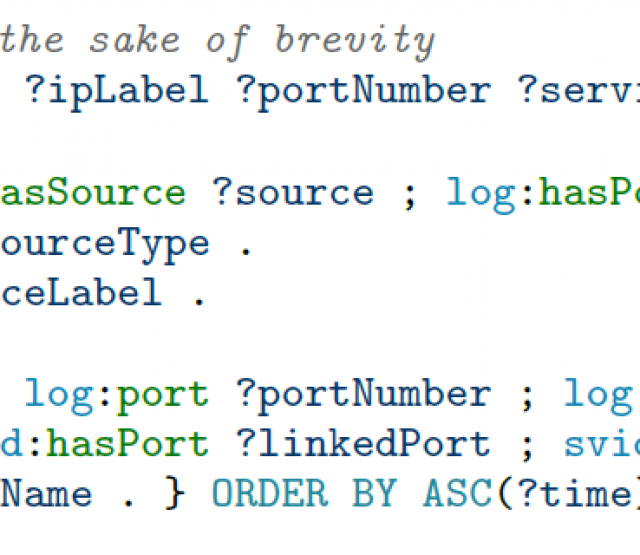
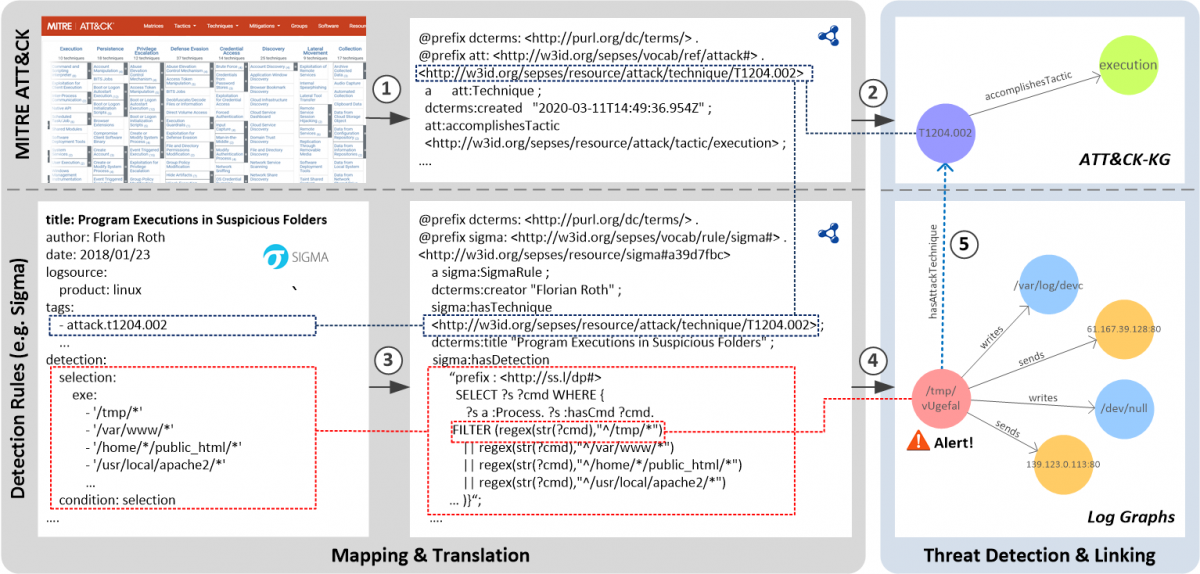
To demonstrate this method, we also introduced a method to translate community-based threat detection rules from sources such as Sigma, into SPARQL queries and link the alerts they produce to adversarial tactics and techniques defined in ATT&CK.
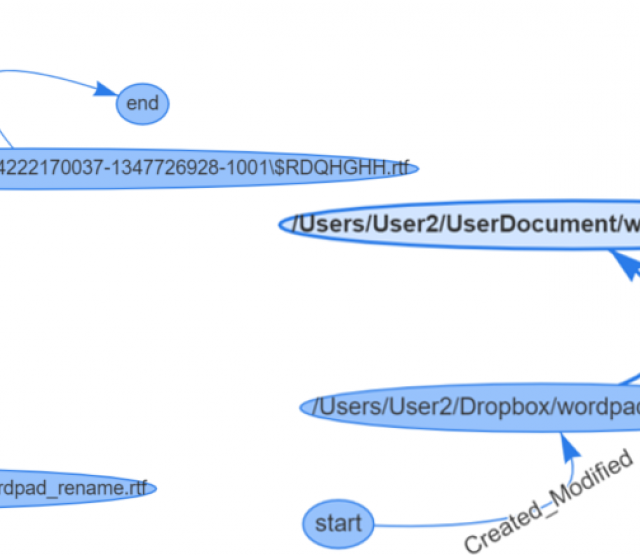
The following figure visualizes an example of threat detection based on translated Sigma rules on RDF Log graphs. Once detected, the respected alerts will be automatically linked to the ATT&CK knowledge graph. For example, node (“/tmp/vUgefal”) is detected as an alert and automatically linked to the attack technique T1204.002.
The constructed ATT&CK knowledge graph makes it possible to explore and integrate additional information from the cybersecurity knowledge graph (e.g. via SPARQL Query federation) such as attack tactics, mitigations, adversary group, and attack patterns (CAPEC).