Förderjahr 2017 / Science Call #1 / ProjektID: / Projekt: SEPSES
The International Conference on Information Security and Privacy Protection (IFIP Sec) is the flagship event of the International Federation for Information Processing (IFIP) Technical Committee 11 on Information Security and Privacy Protection in Information Processing Systems (TC-11). We are very happy that our paper titled “Cross-Platform File System Activity Monitoring and Forensics - A Semantic Approach” has been accepted and will be presented on September 21-23, 2020, in Maribor, Slovenia.
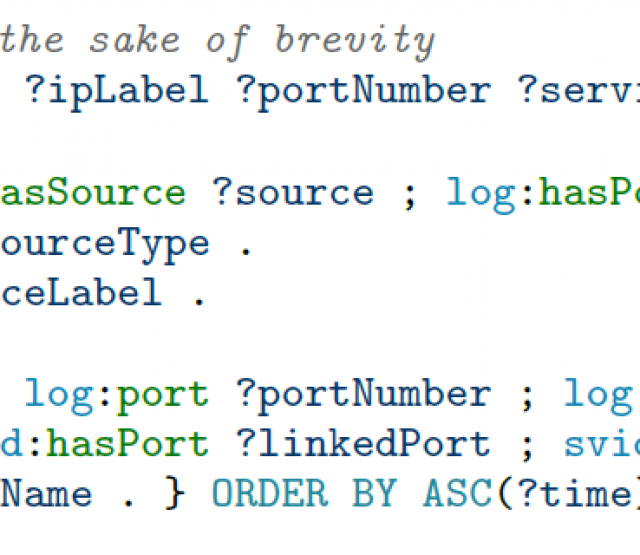
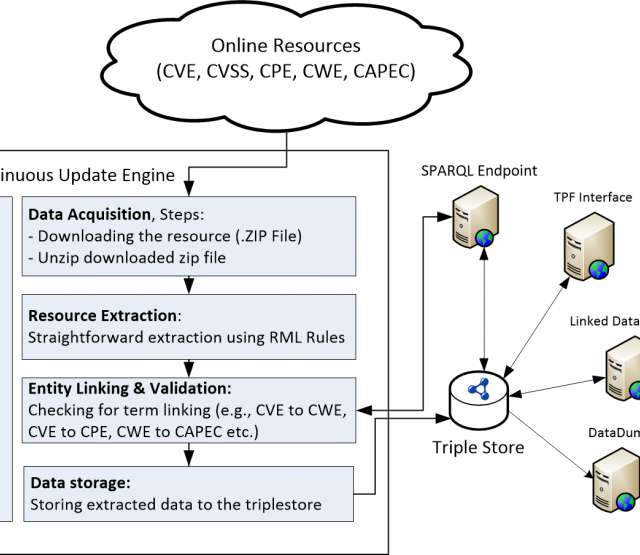
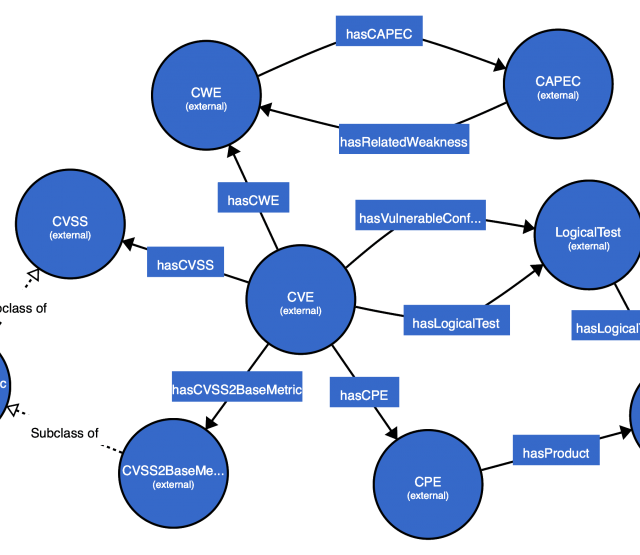
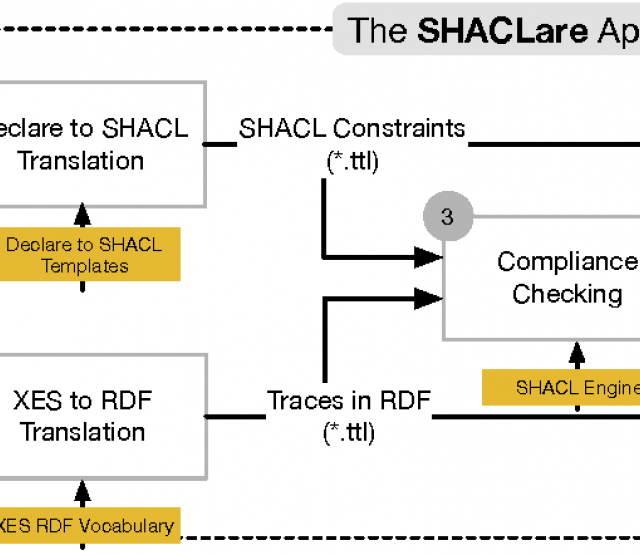
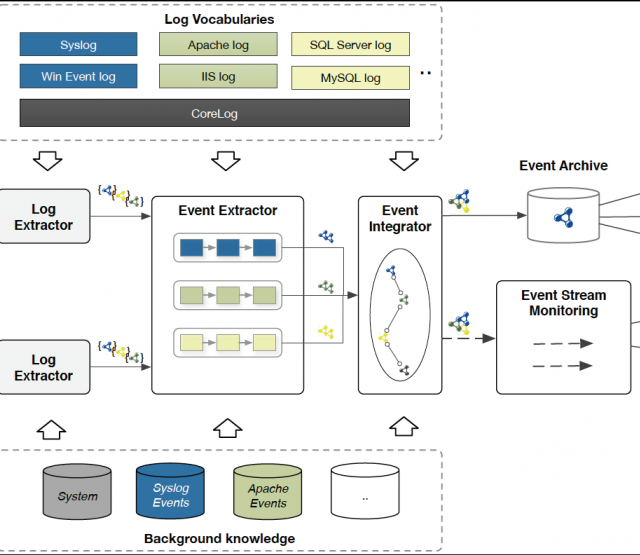
In this paper, we introduce a semantic approach for file system activity monitoring and forensics. We proposed a vocabulary (depicted in Figure 1) for file access information and implement an architecture (shown in Figure 2) for log acquisition, log extraction, linking, and contextualization. The goal of our approach is to tackle the limitation of current existing monitoring and forensics approaches in terms of integration, contextualization and cross-platform interoperability.
Figure 1: File Access Vocabulary
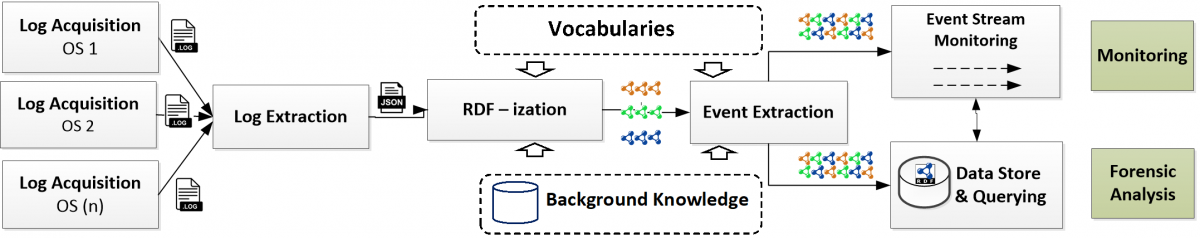
Figure2: Architecture for Semantic-based File Access Monitoring and Forensics
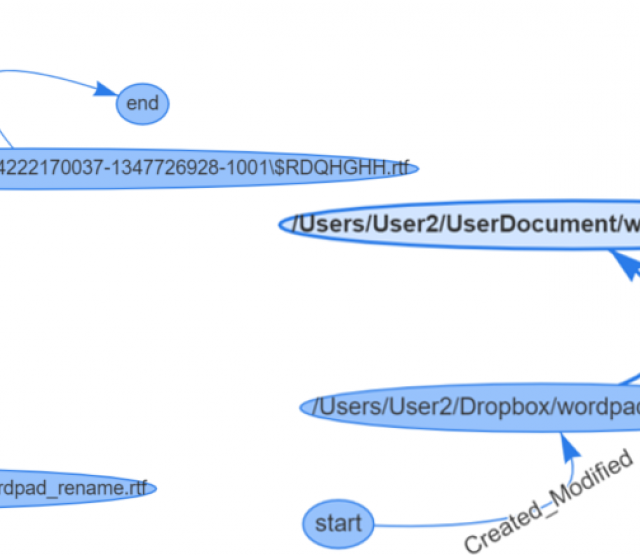
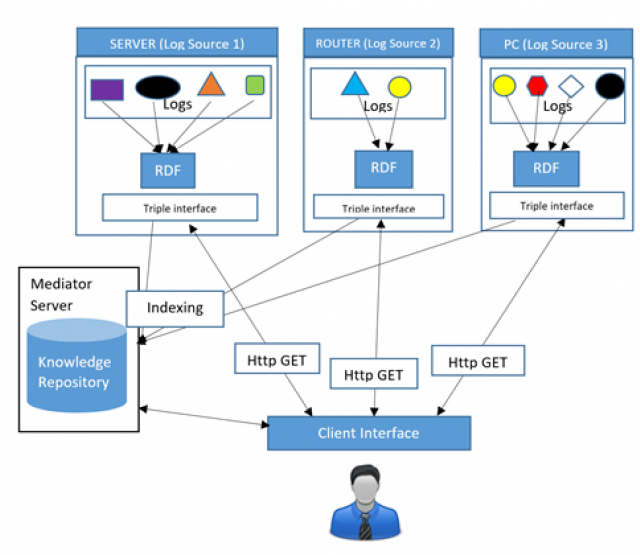
We also demonstrate in two scenarios that our approach can support forensic analysis of data exfiltration and monitoring of sensitive data on vulnerable hosts. In the data exfiltration scenario, we show that using our approach, a security analyst can construct and visualize the access history of files by means of SPARQL queries. Figure 3 shows the visualization of the file access history of an example file.
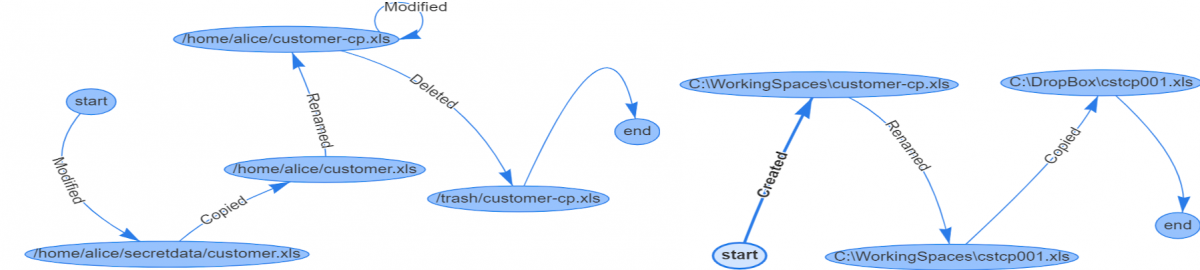
Figure 3: Visualization of File Access History
Furthermore, since our approach supports linking and contextualization, security analysts, for example, can link information from an event (e.g., Login Event) to background knowledge to get more information about hosts, users, etc. In the second scenario, we show that our approach can be used to monitor confidential data movement by combining public vulnerability information (e.g., CVE, CWE, CAPEC) with file activity information. Table 1 shows what sensitive files have been moved to vulnerable hosts.
Table 1: Vulnerability Assessment

Lastly, we also provide an evaluation of our approach by measuring the correctness and completeness of event extraction and event detection. As shown in Figure 4, overall the events (e.g., created, modified, renamed, and deleted) have been successfully detected near 100% for both Windows and Linux platforms with a slightly decreasing rate with an increasing number of events per second. However, only copy events show a lower detection rate caused by incorrect pairings of micro-operations (e.g., “readAttribute”) when two or more sequential copy events appear together in the same time window.
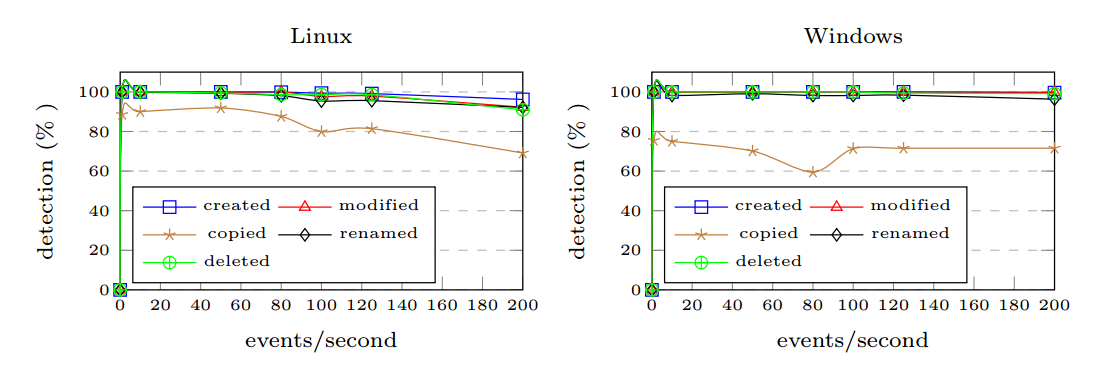
Figure 4: Assessment